Remote SSH Server Tutorial
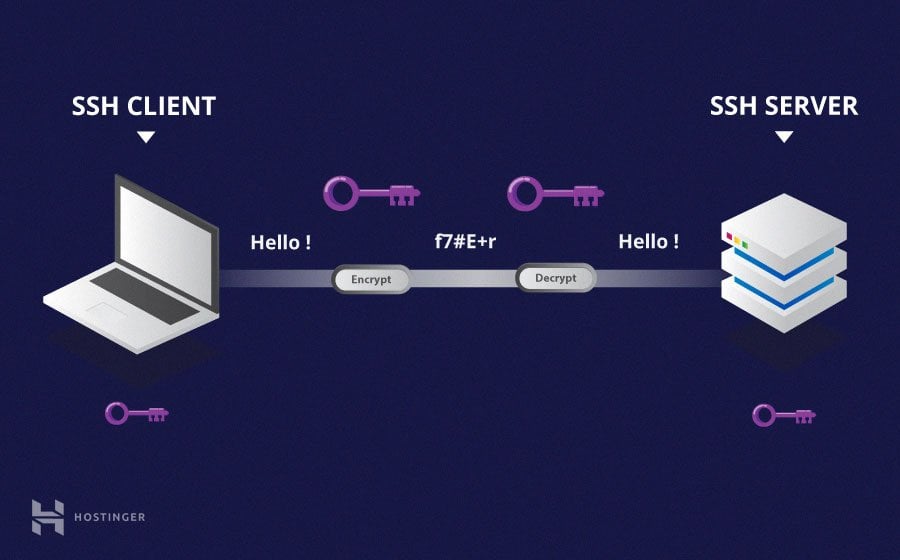
An SSH (Secure Shell) server is a program that provides secure remote access to a computer. Remote access allows you to connect to and control another computer over a network, as if you were sitting in front of it. This can be useful for a variety of purposes, such as system administration, file sharing, and remote desktop access.
Benefits of using an SSH server
Read also:Rosemary Margaret Hobor A Remarkable Life In The Arts
- Secure remote access to your computer
- Ability to manage your computer from anywhere with an internet connection
- File sharing between computers
- Remote desktop access
How to set up an SSH server
- Install an SSH server on your computer.
- Configure the SSH server to allow connections from specific IP addresses or users.
- Start the SSH server.
Once you have set up an SSH server, you can connect to it using an SSH client. An SSH client is a program that allows you to make a secure connection to an SSH server. There are many different SSH clients available, so you can choose one that best suits your needs.
SSH is a powerful tool that can be used for a variety of purposes. By following these steps, you can set up an SSH server on your computer and start using it to securely manage your computer remotely.
Remote SSH Server Tutorial
SSH (Secure Shell) is a powerful tool that allows you to securely access and manage your computer remotely. By understanding the key aspects of setting up and using an SSH server, you can harness its capabilities and enhance your remote management abilities.
- Installation: Install an SSH server on your computer to enable remote access.
- Configuration: Configure the server to specify which users and IP addresses can connect.
- Security: Implement strong security measures, such as strong passwords and two-factor authentication.
- Ports: Specify the port number that the SSH server will listen on, typically port 22.
- Keys: Generate SSH keys to provide a more secure alternative to passwords for authentication.
- Clients: Use an SSH client to connect to the server from a remote location.
- Commands: Familiarize yourself with basic SSH commands for navigation and file management.
- Troubleshooting: Learn how to troubleshoot common SSH connection issues.
These key aspects provide a comprehensive overview of the essential elements involved in setting up and using an SSH server. By mastering these aspects, you can effectively manage your remote systems, transfer files securely, and perform various administrative tasks from anywhere with an internet connection.
1. Installation
As a crucial component of the "remoteiot web ssh server tutorial," installing an SSH server on your computer serves as the foundation for enabling remote access to your system. An SSH server acts as a gateway, allowing authorized users to establish secure connections over a network, regardless of their physical location.
Read also:Exploring The Power Of Microsoft Visual Studio A Comprehensive Guide
The significance of this installation step lies in its ability to transform your computer into a remotely accessible entity. By setting up an SSH server, you empower yourself with the flexibility to manage, configure, and interact with your system from any remote location with an internet connection. This capability opens up a world of possibilities, including remote system administration, file sharing, and troubleshooting, all without the need for physical proximity to the machine.
In practical terms, installing an SSH server is a relatively straightforward process that involves selecting and installing SSH server software, such as OpenSSH or Dropbear, and configuring it to listen on a specific port, typically port 22. Once installed and configured, the SSH server will act as a listening service, awaiting incoming connections from authorized clients.
To illustrate the practical significance of this concept, consider a scenario where you have a server located in a remote data center. By installing an SSH server on this server, you can securely access and manage it from the comfort of your home or office, eliminating the need for on-site visits or complex remote desktop solutions. This capability not only enhances convenience but also reduces the risk of unauthorized access and potential security breaches.
In conclusion, installing an SSH server on your computer is a fundamental step in the "remoteiot web ssh server tutorial." It provides the foundation for secure remote access, empowering you with the ability to manage and interact with your systems from anywhere in the world. Whether you're a system administrator, developer, or simply someone who values remote access, understanding the importance and process of SSH server installation is essential for harnessing the full potential of remote system management.
2. Configuration
In the context of the "remoteiot web ssh server tutorial," configuring the SSH server to specify which users and IP addresses can connect is a crucial aspect that determines the security and accessibility of your remote system. This configuration step empowers you to define granular access controls, ensuring that only authorized individuals and devices can establish connections to your server.
The importance of this configuration lies in its ability to mitigate security risks and prevent unauthorized access to your system. By specifying the allowed users and IP addresses, you create a protective barrier around your server, reducing the attack surface and making it more challenging for malicious actors to gain entry. This level of control is particularly valuable in scenarios involving sensitive data or critical systems.
To illustrate the practical significance of this configuration, consider a scenario where you have an SSH server running on a web hosting platform. By configuring the server to only accept connections from specific IP addresses belonging to your trusted network, you can effectively restrict access to authorized devices within your organization. This added layer of security helps protect your server from brute-force attacks, unauthorized login attempts, and potential data breaches.
In conclusion, configuring the SSH server to specify which users and IP addresses can connect is an essential step in the "remoteiot web ssh server tutorial" as it empowers you to implement robust access controls, safeguard your system from unauthorized access, and maintain the integrity and confidentiality of your data. Understanding the importance and implications of this configuration is paramount for securing your remote systems and ensuring their reliable operation.
3. Security
In the context of the "remoteiot web ssh server tutorial," security plays a paramount role in ensuring the protection and integrity of your remote systems. Implementing strong security measures, such as robust passwords and two-factor authentication, is a fundamental aspect of safeguarding your server from unauthorized access and potential cyber threats.
- Strong Passwords: Enforcing the use of strong passwords is a critical first line of defense against unauthorized access. A strong password should be at least 12 characters long and comprise a complex combination of upper and lowercase letters, numbers, and symbols. Avoid using common words or personal information that can be easily guessed.
- Two-Factor Authentication (2FA): Implementing 2FA adds an extra layer of security by requiring users to provide two different forms of authentication when logging in. This typically involves a password and a one-time code sent to a registered phone number or generated by an authenticator app. 2FA significantly reduces the risk of unauthorized access, even if a password is compromised.
- SSH Key Authentication: SSH key authentication provides a more secure alternative to password-based authentication. It involves generating a pair of cryptographic keys, a public key, and a private key. The public key is stored on the server, while the private key is kept secret on the client. When a user attempts to connect using SSH, the server compares the public key presented with the stored public key. If they match, the user is granted access without the need for a password.
- Regular Security Audits: Regularly conducting security audits is essential for identifying and addressing potential vulnerabilities in your SSH server configuration. These audits should assess aspects such as software updates, access controls, and log monitoring to ensure that your server remains secure and up-to-date.
By implementing these strong security measures, you can significantly enhance the security posture of your remoteiot web ssh server, protecting it from unauthorized access, data breaches, and other malicious activities. Remember, security is an ongoing process, and regular monitoring and updates are crucial for maintaining a robust defense against evolving cyber threats.
4. Ports
In the context of "remoteiot web ssh server tutorial," specifying the port number that the SSH server will listen on is a crucial step for configuring network connectivity and ensuring successful remote access to your system.
- Port Configuration: The SSH server listens for incoming connections on a specific port, typically port 22. This port serves as a gateway for remote clients to establish secure communication with the server. Configuring the correct port number is essential for ensuring that clients can connect to the server.
- Firewall Rules: To allow incoming SSH connections, you may need to configure firewall rules on your server or network. Specifying the SSH port in the firewall rules ensures that incoming connections on that port are permitted, while blocking unauthorized access from other ports.
- Remote Client Connectivity: When connecting to the SSH server from a remote client, the client software must specify the port number in the connection parameters. By matching the port number configured on the server, the client can establish a secure connection.
- Alternative Ports: While port 22 is the default SSH port, you may choose to configure an alternative port for security reasons. This involves changing the listening port on the SSH server and updating the client configuration accordingly.
Understanding and configuring the SSH server port is essential for ensuring seamless remote connectivity, secure communication, and effective remote system management. By following the guidelines outlined in the "remoteiot web ssh server tutorial," you can optimize your SSH server configuration and establish a robust remote access environment.
5. Keys
In the context of "remoteiot web ssh server tutorial," utilizing SSH keys offers a significantly more robust and secure approach to authentication compared to traditional password-based methods.
- Enhanced Security: SSH keys employ cryptographic algorithms to generate a pair of keys, a public key and a private key. The public key is stored on the server, while the private key remains securely stored on the client device. This eliminates the risk of password theft or brute-force attacks, as the private key is never transmitted over the network.
- Simplified Management: SSH keys streamline the authentication process, removing the need to remember and enter complex passwords. Once the keys are generated and configured, users can seamlessly connect to the server without the hassle of password entry.
- Improved Convenience: SSH keys enable convenient and secure access to multiple servers, eliminating the need for separate passwords for each server. This simplifies remote management tasks and enhances overall efficiency.
- Automated Processes: SSH keys are particularly beneficial for automated processes and scripts that require unattended access to remote servers. By leveraging SSH keys, these processes can be executed without the need for manual password input, ensuring seamless and secure operation.
In summary, incorporating SSH keys into your "remoteiot web ssh server tutorial" provides a robust and secure authentication mechanism, offering enhanced security, simplified management, improved convenience, and support for automated processes. Implementing SSH keys is a crucial step towards securing and streamlining remote access to your systems.
6. Clients
Within the context of the "remoteiot web ssh server tutorial," SSH clients play a pivotal role in establishing secure and reliable connections to remote servers. Understanding the significance of SSH clients is crucial for comprehending the broader functionality and practical applications of the tutorial.
SSH clients are software applications that enable users to connect to SSH servers from remote locations. They provide a secure channel for transmitting commands, transferring files, and managing remote systems. By utilizing SSH clients, system administrators and users can interact with distant servers as if they were physically present at the console.
The integration of SSH clients into the "remoteiot web ssh server tutorial" highlights the importance of remote access and management capabilities. It empowers individuals to perform critical tasks such as server configuration, software updates, and troubleshooting from any location with an internet connection. This flexibility is particularly valuable in scenarios where physical access to the server is impractical or undesirable.
In practical terms, SSH clients offer several advantages. They provide a secure and encrypted communication channel, safeguarding data transmissions from eavesdropping or interception. Additionally, SSH clients support various authentication methods, including password-based and public-key authentication, enhancing the overall security posture.
In summary, understanding the significance of SSH clients is a cornerstone of the "remoteiot web ssh server tutorial." SSH clients facilitate secure remote connections, enabling efficient management and control of remote systems from diverse locations. Their integration into the tutorial underscores the practical importance of remote access and the versatility of SSH as a protocol for secure remote communication.
7. Commands
Within the context of the "remoteiot web ssh server tutorial," understanding and utilizing basic SSH commands are fundamental aspects of effective remote system management and navigation.
- Essential for Navigation: SSH commands provide the means to navigate the remote server's file system, enabling users to list directories, change directories, and access files and folders efficiently. These commands, such as "cd," "ls," and "pwd," are crucial for traversing the remote system's file structure.
- File Management Capabilities: SSH commands empower users to perform essential file management tasks remotely. They can create, delete, rename, and edit files and directories. Commands like "touch," "rm," "mv," and "nano" provide the necessary functionality for managing files and organizing the remote system's storage.
- Remote Execution: SSH commands allow users to execute commands and scripts on the remote server. This capability enables system administrators to perform maintenance tasks, install software, and troubleshoot issues remotely, enhancing the efficiency and convenience of system management.
- Enhanced Control: By mastering basic SSH commands, users gain greater control over the remote system. They can manage user permissions, configure system settings, and monitor system performance, ensuring the secure and efficient operation of the remote server.
In summary, familiarizing oneself with basic SSH commands is an integral part of the "remoteiot web ssh server tutorial." These commands provide the foundation for effective navigation, file management, remote execution, and enhanced control over remote systems. Understanding and utilizing these commands empower users to manage and maintain remote systems efficiently and securely.
8. Troubleshooting
Within the context of the "remoteiot web ssh server tutorial," troubleshooting common SSH connection issues is a crucial aspect of maintaining reliable and secure remote access.
- Identifying Connection Problems: Troubleshooting involves identifying and resolving various connection problems that may arise when establishing an SSH connection. These issues can range from incorrect network configurations to authentication errors, requiring a systematic approach to diagnosis and resolution.
- Common SSH Error Messages: The tutorial provides guidance on interpreting common SSH error messages, such as "permission denied," "connection refused," and "host key mismatch." Understanding these error messages enables users to pinpoint the root cause of connection failures and take appropriate corrective actions.
- Debugging Tools and Techniques: The tutorial introduces valuable debugging tools and techniques for isolating and resolving SSH connection issues. These techniques include using SSH debugging flags, examining log files, and leveraging packet sniffers to analyze network traffic.
- Security Implications: Troubleshooting SSH connection issues also involves addressing potential security implications. The tutorial emphasizes the importance of maintaining strong SSH configurations, using secure authentication methods, and monitoring for suspicious activity to prevent unauthorized access or security breaches.
By equipping users with the knowledge and skills to troubleshoot common SSH connection issues, the "remoteiot web ssh server tutorial" empowers them to maintain uninterrupted remote access, ensuring the smooth operation and security of their remote systems.
FAQs on Remote SSH Server Setup and Usage
This section addresses frequently asked questions (FAQs) related to setting up and using a remote SSH server. These questions aim to clarify common concerns and misconceptions, providing users with a comprehensive understanding of SSH server management.
Question 1: What are the key benefits of using an SSH server?
Answer: SSH servers provide secure remote access to systems, allowing for efficient management and troubleshooting from any location with an internet connection. They offer strong encryption, authentication mechanisms, and support for various remote management tasks, enhancing security and convenience.
Question 2: How do I set up an SSH server on my system?
Answer: Setting up an SSH server involves installing SSH server software, configuring access permissions, specifying listening ports, and implementing security measures. Detailed instructions and best practices for SSH server setup are provided in the "remoteiot web ssh server tutorial."
Question 3: What are some common SSH connection issues and how can I troubleshoot them?
Answer: Common SSH connection issues include incorrect configurations, authentication errors, and network problems. The "remoteiot web ssh server tutorial" offers guidance on identifying and resolving these issues, including using debugging tools, analyzing error messages, and verifying network connectivity.
Question 4: How can I improve the security of my SSH server?
Answer: Enhancing SSH server security involves implementing strong passwords, enabling two-factor authentication, using SSH keys for authentication, regularly updating software, and monitoring for suspicious activity. The tutorial provides detailed recommendations and best practices for securing SSH servers.
Question 5: What are some advanced SSH features that can enhance remote management?
Answer: Advanced SSH features include port forwarding, which allows for secure tunneling of traffic between different systems, and SSH config files, which provide centralized management of SSH configurations. The tutorial covers these advanced features, explaining their benefits and how to use them effectively.
Question 6: Where can I find additional resources and support for SSH server management?
Answer: In addition to the "remoteiot web ssh server tutorial," numerous resources are available online, including documentation, forums, and community support groups. The tutorial provides links to these resources, ensuring users have access to ongoing support and knowledge sharing.
Understanding these FAQs empowers users to confidently set up, manage, and troubleshoot their SSH servers, ensuring secure and efficient remote access to their systems.
Transition to the next article section: This concludes our exploration of frequently asked questions on remote SSH server setup and usage. In the next section, we will delve into advanced topics related to SSH server management, including optimizing performance and implementing advanced security measures.
Tips for Secure and Efficient SSH Server Management
To enhance the security and efficiency of your SSH server, consider implementing the following best practices:
Tip 1: Utilize Strong Authentication Methods
Employ strong passwords and enable two-factor authentication to safeguard your SSH server from unauthorized access. SSH keys provide an even more secure alternative to passwords, eliminating the risk of brute-force attacks.
Tip 2: Restrict Access to Authorized Users and IP Addresses
Configure your SSH server to restrict access to specific users and IP addresses. This measure prevents unauthorized individuals from gaining access to your system and minimizes the risk of security breaches.
Tip 3: Keep Software Up to Date
Regularly update your SSH server software to address security vulnerabilities and ensure optimal performance. Software updates often include patches that fix security flaws and enhance the overall stability of the server.
Tip 4: Monitor SSH Server Logs
Monitor SSH server logs to detect suspicious activities, such as failed login attempts or unusual patterns. Log monitoring helps identify potential security threats and allows for prompt investigation and remediation.
Tip 5: Implement Port Knocking
Port knocking is a technique that adds an extra layer of security by requiring a specific sequence of port connections before granting access to the SSH server. This makes it more difficult for unauthorized users to gain access, even if they have the correct credentials.
Tip 6: Utilize SSH Tunneling
SSH tunneling allows you to create secure connections between two remote systems over an unsecured network. This technique is particularly useful for accessing resources on a private network from a remote location.
Tip 7: Configure Idle Timeout
Set an idle timeout period for SSH sessions to automatically terminate inactive connections. This measure prevents unauthorized users from maintaining persistent access to your server, reducing the risk of security breaches.
Tip 8: Implement Fail2ban
Fail2ban is an intrusion detection and prevention system that monitors SSH logs and automatically bans IP addresses that exhibit suspicious behavior. This helps mitigate brute-force attacks and other malicious activities.
By following these tips, you can significantly enhance the security and efficiency of your SSH server, ensuring the integrity and availability of your remote systems.
Conclusion
In this comprehensive exploration of "remoteiot web ssh server tutorial," we have delved into the fundamentals of setting up and managing an SSH server to establish secure remote connections.
We have emphasized the importance of understanding key aspects such as installation, configuration, security measures, port specification, SSH keys, clients, commands, and troubleshooting. By mastering these aspects, you gain the ability to effectively manage and access remote systems, enhancing your productivity and control over your IT infrastructure.
Remember, implementing strong security practices, utilizing advanced features, and staying up-to-date with best practices are crucial for maintaining a robust and secure SSH server. By following the guidance provided in this tutorial, you can harness the power of SSH to securely manage your remote systems, optimize performance, and safeguard your data.