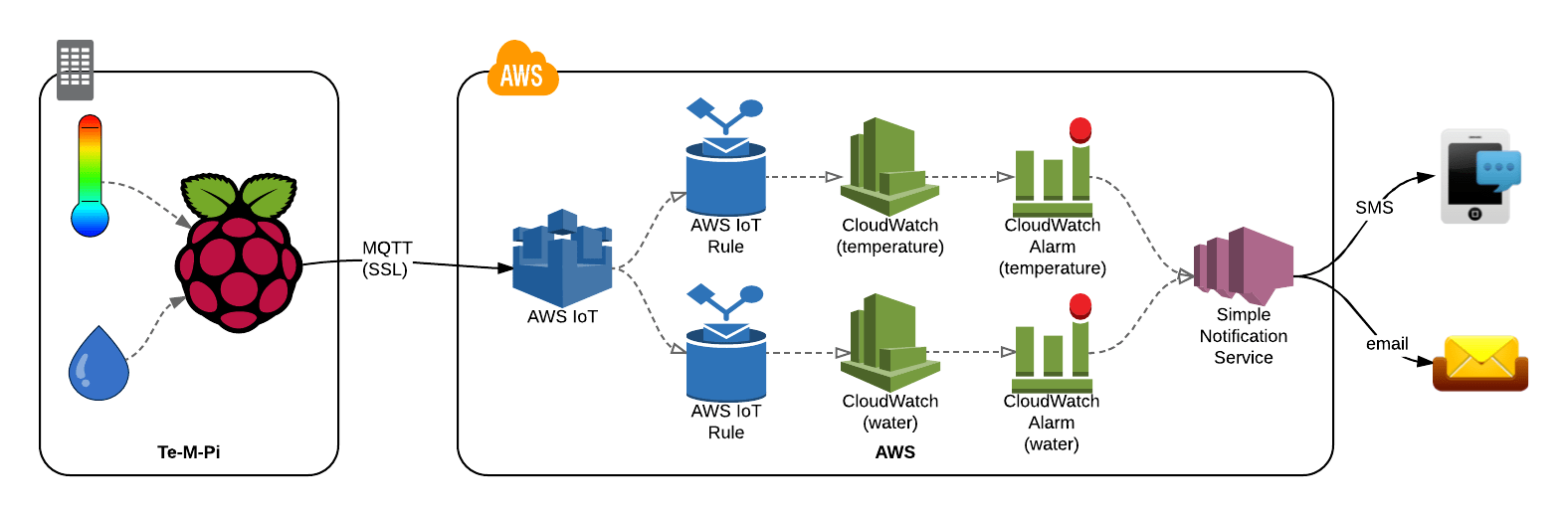
To securely connect a remote Raspberry Pi device to an AWS VPC (Virtual Private Cloud) using the IoT service, you can use a combination of AWS IoT Device SDK, AWS IoT Core, and a VPN (Virtual Private Network) connection. This allows you to securely communicate with and manage your Raspberry Pi device from the cloud, while isolating it from the public internet.
To establish a secure connection, you will need to configure your Raspberry Pi with the AWS IoT Device SDK, which provides libraries and tools for connecting devices to AWS IoT Core. AWS IoT Core is a managed cloud service that allows you to connect and manage IoT devices securely. You will also need to set up a VPN connection between your Raspberry Pi and your VPC, which will create a secure tunnel for data transmission.
Once you have configured these components, you can securely connect your Raspberry Pi to your AWS VPC and start sending and receiving data. This setup provides several benefits, including:
Read also:All You Need To Know About Sherrill Sajak A Tale Of Talent And Tenacity
- Secure communication between your Raspberry Pi and AWS IoT Core
- Isolation of your Raspberry Pi from the public internet
- Centralized management of your Raspberry Pi and other IoT devices in your VPC
Securely Connect Remote IoT VPC Raspberry Pi AWS Download
Connecting Raspberry Pi devices to AWS IoT securely is crucial for remote IoT applications. Here are eight key aspects to consider:
- Authentication: Verify the identity of devices connecting to AWS IoT.
- Authorization: Control access to AWS IoT resources based on device identity.
- Encryption: Protect data in transit between devices and AWS IoT.
- Isolation: Keep Raspberry Pi devices isolated from the public internet.
- Monitoring: Track and analyze device behavior for security threats.
- Updates: Regularly update device software and firmware for security patches.
- Credentials: Manage and protect device credentials securely.
- Compliance: Adhere to industry security standards and regulations.
By addressing these aspects, organizations can establish secure connections between remote Raspberry Pi devices and AWS IoT, ensuring the confidentiality, integrity, and availability of data and devices.
1. Authentication: Verify the identity of devices connecting to AWS IoT.
Authentication is a critical aspect of securely connecting remote IoT devices to AWS IoT. It ensures that only authorized devices can connect to the AWS IoT service and access its resources. Without proper authentication, unauthorized devices could gain access to sensitive data and disrupt the operation of the IoT system.
AWS IoT provides several mechanisms for authenticating devices, including:
- X.509 certificates
- JWT (JSON Web Tokens)
- Custom authentication methods
The choice of authentication mechanism depends on the specific requirements of the IoT system. For example, X.509 certificates provide a high level of security but require a public key infrastructure (PKI) to manage the certificates. JWTs are a lightweight alternative to X.509 certificates but may not be suitable for applications that require a high level of security.
Once a device has been authenticated, AWS IoT issues the device a unique identifier that can be used to authorize the device to access specific resources. This authorization process helps to ensure that devices can only access the resources that they are authorized to access.
Read also:Daily Verse Inspiration And Guidance For Your Day
By implementing a robust authentication mechanism, organizations can help to protect their IoT systems from unauthorized access and ensure the secure connection of remote IoT devices to AWS IoT.
2. Authorization: Control access to AWS IoT resources based on device identity.
Authorization is the process of controlling access to resources based on the identity of the requester. In the context of securely connecting remote IoT devices to AWS IoT, authorization ensures that devices can only access the resources that they are authorized to access.
- Identity-based access control: AWS IoT uses identity-based access control to authorize devices. This means that devices are identified by their unique identifiers, and access to resources is granted or denied based on the identity of the device.
- Device policies: AWS IoT uses device policies to specify the permissions that are granted to devices. Device policies are JSON documents that define the resources that a device can access and the operations that the device can perform on those resources.
- Resource-based permissions: AWS IoT also uses resource-based permissions to control access to resources. Resource-based permissions are defined in AWS Identity and Access Management (IAM) policies. IAM policies specify the permissions that are granted to principals (such as users, groups, and roles) to access specific resources.
- Authentication and authorization: Authentication and authorization are two important security mechanisms that work together to protect AWS IoT resources. Authentication verifies the identity of a device, while authorization controls access to resources based on the identity of the device.
By implementing a robust authorization mechanism, organizations can help to protect their IoT systems from unauthorized access and ensure the secure connection of remote IoT devices to AWS IoT.
3. Encryption: Protect data in transit between devices and AWS IoT.
Encryption is a crucial aspect of securely connecting remote IoT devices to AWS IoT. It ensures that data transmitted between devices and AWS IoT is protected from unauthorized access, eavesdropping, and tampering.
- Data confidentiality: Encryption protects the confidentiality of data by ensuring that only authorized parties can access it. This is especially important for sensitive data, such as customer information, financial data, and trade secrets.
- Data integrity: Encryption protects the integrity of data by ensuring that it is not modified or corrupted during transmission. This helps to prevent unauthorized changes to data, which could lead to incorrect decisions or even financial losses.
- Data authenticity: Encryption protects the authenticity of data by ensuring that it comes from the intended source. This helps to prevent spoofing attacks, where an attacker impersonates a legitimate device or user to gain unauthorized access to data.
AWS IoT provides several mechanisms for encrypting data in transit, including:
- TLS/SSL: TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols that provide secure communication between devices and AWS IoT.
- MQTT over WebSockets: MQTT over WebSockets is a secure protocol that combines the MQTT (Message Queuing Telemetry Transport) protocol with WebSockets. It provides a secure and efficient way to connect devices to AWS IoT.
By implementing encryption, organizations can help to protect their IoT systems from unauthorized access, eavesdropping, and tampering. This ensures the secure connection of remote IoT devices to AWS IoT and protects the confidentiality, integrity, and authenticity of data.
4. Isolation: Keep Raspberry Pi devices isolated from the public internet.
Isolating Raspberry Pi devices from the public internet is a critical aspect of securely connecting them to AWS IoT. By keeping devices isolated, organizations can reduce the risk of unauthorized access, malware infections, and other security threats.
- Reduced attack surface: Isolating devices from the public internet reduces the attack surface that is exposed to potential threats. This makes it more difficult for attackers to find and exploit vulnerabilities in devices.
- Protection from malware: Isolating devices from the public internet can help to protect them from malware infections. Malware is often spread through malicious websites and email attachments. By preventing devices from accessing the public internet, organizations can reduce the risk of malware infections.
- Compliance with regulations: Isolating devices from the public internet can help organizations to comply with regulations that require the protection of sensitive data. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare organizations to protect the privacy and security of patient health information.
- Improved security posture: Isolating devices from the public internet can improve the overall security posture of an organization. By reducing the risk of unauthorized access, malware infections, and other security threats, organizations can help to protect their data and systems.
There are several ways to isolate Raspberry Pi devices from the public internet, including:
- Using a VPN: A VPN (Virtual Private Network) can be used to create a secure tunnel between a device and a private network. This allows the device to access the private network without exposing it to the public internet.
- Using a firewall: A firewall can be used to block unauthorized access to devices from the public internet. Firewalls can be configured to allow only specific types of traffic, such as traffic from specific IP addresses or ports.
- Using a DMZ: A DMZ (Demilitarized Zone) is a network segment that is isolated from both the public internet and the private network. Devices in a DMZ can be accessed from the public internet, but they cannot access the private network. This provides an additional layer of security for devices that need to be accessible from the public internet.
By implementing isolation measures, organizations can help to protect their Raspberry Pi devices from unauthorized access, malware infections, and other security threats. This helps to ensure the secure connection of remote IoT devices to AWS IoT and protects the confidentiality, integrity, and availability of data.
5. Monitoring: Track and analyze device behavior for security threats.
Monitoring is a critical aspect of securely connecting remote IoT devices to AWS IoT. By tracking and analyzing device behavior, organizations can identify and mitigate security threats, such as unauthorized access, malware infections, and data breaches.
AWS IoT provides several tools and services for monitoring device behavior, including:
- AWS IoT Device Defender: AWS IoT Device Defender is a managed service that helps organizations to monitor and secure their IoT devices. Device Defender uses machine learning to detect anomalous device behavior and generate security alerts.
- AWS IoT Analytics: AWS IoT Analytics is a managed service that allows organizations to analyze data from their IoT devices. IoT Analytics can be used to identify trends and patterns in device behavior, which can help organizations to identify and mitigate security threats.
By implementing a robust monitoring program, organizations can help to protect their IoT systems from security threats. Monitoring helps to identify and mitigate threats early on, before they can cause significant damage. This helps to ensure the secure connection of remote IoT devices to AWS IoT and protects the confidentiality, integrity, and availability of data.
Here are some real-life examples of how monitoring can be used to identify and mitigate security threats:
- A manufacturing company uses AWS IoT Device Defender to monitor its IoT devices for unauthorized access. Device Defender detects an attempt to access a device from an unknown IP address. The company investigates the incident and discovers that an attacker is trying to gain access to the device to steal sensitive data.
- A healthcare organization uses AWS IoT Analytics to analyze data from its IoT devices. IoT Analytics identifies a trend in device behavior that suggests that a malware infection is spreading through the devices. The organization investigates the incident and discovers that a malicious actor has infected the devices with a ransomware virus.
These examples illustrate the importance of monitoring device behavior for security threats. By implementing a robust monitoring program, organizations can help to protect their IoT systems from security threats and ensure the secure connection of remote IoT devices to AWS IoT.
6. Updates: Regularly update device software and firmware for security patches.
Regularly updating device software and firmware is a critical aspect of securely connecting remote IoT devices to AWS IoT. By keeping devices up to date with the latest security patches, organizations can reduce the risk of vulnerabilities being exploited by attackers.
- Reduced risk of vulnerabilities: Security patches are released to fix vulnerabilities in software and firmware. By applying security patches, organizations can reduce the risk of these vulnerabilities being exploited by attackers.
- Improved security posture: Keeping devices up to date with the latest security patches improves the overall security posture of an organization. By reducing the risk of vulnerabilities being exploited, organizations can help to protect their data and systems.
- Compliance with regulations: Some regulations require organizations to keep their devices up to date with the latest security patches. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare organizations to implement security measures to protect the privacy and security of patient health information.
- Improved device performance: In addition to security benefits, updating device software and firmware can also improve device performance. Device manufacturers often release updates that include performance improvements and bug fixes.
Organizations can implement a variety of strategies to ensure that their devices are regularly updated with the latest security patches. These strategies include:
- Automated updates: Many devices support automated updates. This means that the device will automatically download and install security patches as they become available.
- Manual updates: For devices that do not support automated updates, organizations can manually update the devices by downloading the latest security patches from the device manufacturer's website.
- Centralized management: Organizations can use centralized management tools to manage the updates of their devices. These tools can be used to schedule updates, deploy updates, and monitor the status of updates.
By implementing a strategy to regularly update device software and firmware, organizations can help to protect their IoT systems from security threats. This helps to ensure the secure connection of remote IoT devices to AWS IoT and protects the confidentiality, integrity, and availability of data.
7. Credentials: Manage and protect device credentials securely.
Managing and protecting device credentials securely is a critical aspect of securely connecting remote IoT devices to AWS IoT. Device credentials are used to authenticate devices to AWS IoT and authorize them to access AWS IoT resources. If device credentials are compromised, attackers could gain unauthorized access to IoT devices and AWS IoT resources, which could lead to data breaches, device hijacking, and other security incidents.
There are several best practices for managing and protecting device credentials:
- Use strong and unique passwords or keys for each device.
- Store device credentials securely in a password manager or other secure location.
- Limit the number of people who have access to device credentials.
- Rotate device credentials regularly.
- Monitor for suspicious activity related to device credentials.
By following these best practices, organizations can help to protect their IoT systems from security threats and ensure the secure connection of remote IoT devices to AWS IoT.
Here is a real-life example of the importance of managing and protecting device credentials securely:
A manufacturing company was using AWS IoT to connect its IoT devices to the cloud. The company stored the device credentials in a plain text file on a shared network drive. An attacker gained access to the network drive and stole the device credentials. The attacker used the stolen credentials to gain unauthorized access to the IoT devices and steal sensitive data.
This example illustrates the importance of managing and protecting device credentials securely. By following the best practices outlined above, organizations can help to protect their IoT systems from security threats and ensure the secure connection of remote IoT devices to AWS IoT.
8. Compliance: Adhere to industry security standards and regulations.
Compliance with industry security standards and regulations is a critical aspect of securely connecting remote IoT devices to AWS IoT. By adhering to these standards and regulations, organizations can help to ensure that their IoT systems are secure and that they are meeting their legal and regulatory obligations.
There are a number of industry security standards and regulations that are relevant to IoT, including:
- ISO 27001: This is an international standard that provides a framework for implementing an information security management system (ISMS). An ISMS helps organizations to manage and protect their information assets, including their IoT devices and data.
- NIST Cybersecurity Framework: This is a framework developed by the National Institute of Standards and Technology (NIST) that provides guidance on how to protect critical infrastructure from cyber threats. The framework includes a number of best practices that can be applied to IoT systems.
- GDPR: This is a European Union regulation that protects the personal data of EU citizens. GDPR has a number of requirements that organizations must comply with if they are processing personal data, including data that is collected from IoT devices.
By complying with these standards and regulations, organizations can help to protect their IoT systems from security threats and ensure that they are meeting their legal and regulatory obligations. This helps to ensure the secure connection of remote IoT devices to AWS IoT and protects the confidentiality, integrity, and availability of data.
Here is a real-life example of the importance of compliance with industry security standards and regulations:
A healthcare organization was using AWS IoT to connect its IoT devices to the cloud. The organization was required to comply with HIPAA, which is a US regulation that protects the privacy and security of patient health information. The organization implemented a number of measures to comply with HIPAA, including encrypting data in transit and at rest, and implementing access controls to protect patient data. By complying with HIPAA, the organization was able to protect the privacy and security of its patients' health information.
This example illustrates the importance of compliance with industry security standards and regulations. By complying with these standards and regulations, organizations can help to protect their IoT systems from security threats and ensure that they are meeting their legal and regulatory obligations.
FAQs on Securely Connecting Remote IoT VPC Raspberry Pi to AWS
This section addresses frequently asked questions regarding the secure connection of remote Raspberry Pi devices to AWS IoT through a VPC. It provides clear and concise answers to common concerns and misconceptions.
Question 1: What are the primary benefits of securely connecting a Raspberry Pi to AWS IoT via a VPC?
Answer: Establishing a secure connection offers several advantages, including enhanced data protection during transmission, isolation of the Raspberry Pi from the public internet, centralized management of devices within the VPC, and simplified monitoring and maintenance.
Question 2: What is the significance of using a Virtual Private Network (VPN) in this setup?
Answer: A VPN establishes a secure tunnel between the Raspberry Pi and the VPC, encrypting data transmission and providing an additional layer of protection against unauthorized access and eavesdropping.
Question 3: How does AWS IoT Device SDK contribute to the security of the connection?
Answer: The AWS IoT Device SDK provides libraries and tools specifically designed for securely connecting devices to AWS IoT. It enables authentication, authorization, and secure data exchange between the Raspberry Pi and AWS IoT.
Question 4: What measures can be taken to ensure the secure management of device credentials?
Answer: Best practices include using strong and unique credentials, storing them securely, limiting access to authorized personnel, rotating credentials regularly, and monitoring for suspicious activities related to credentials.
Question 5: How does adhering to industry security standards and regulations contribute to the overall security of the connection?
Answer: Compliance with standards such as ISO 27001, NIST Cybersecurity Framework, and GDPR ensures alignment with established best practices, reduces the risk of security breaches, and helps organizations meet legal and regulatory obligations.
Question 6: What are some real-world examples that demonstrate the importance of secure remote connectivity for IoT devices?
Answer: Secure connectivity safeguards sensitive data, prevents unauthorized access to devices, and enables remote monitoring and control, as illustrated by use cases such as secure data collection from remote sensors and remote management of industrial equipment.
In summary, securely connecting a Raspberry Pi to AWS IoT via a VPC offers numerous advantages, including enhanced data protection, device isolation, centralized management, and compliance with industry standards. By implementing best practices and adhering to security guidelines, organizations can ensure the secure and reliable operation of their remote IoT devices.
Transition to the next article section: Exploring Advanced Techniques for Securely Connecting Remote IoT Devices
Tips for Securely Connecting Remote IoT VPC Raspberry Pi to AWS
Implementing robust security measures is crucial for establishing a secure connection between a remote Raspberry Pi device and AWS IoT via a Virtual Private Cloud (VPC). Here are some practical tips to enhance the security of your IoT setup:
Tip 1: Implement Strong Authentication and Authorization Mechanisms
Use robust authentication methods like X.509 certificates or JWT (JSON Web Tokens) to verify the identity of devices connecting to AWS IoT. Implement authorization policies to control access to AWS IoT resources based on device identity and permissions.
Tip 2: Encrypt Data in Transit and at Rest
Encrypt data transmitted between the Raspberry Pi device and AWS IoT using protocols like TLS/SSL or MQTT over WebSockets. Additionally, encrypt data stored on the device or in the cloud using encryption algorithms like AES-256.
Tip 3: Isolate the Raspberry Pi from the Public Internet
Utilize a VPN or firewall to isolate the Raspberry Pi from the public internet, reducing the attack surface and preventing unauthorized access to the device.
Tip 4: Regularly Update Device Software and Firmware
Keep the Raspberry Pi device and its software up to date with the latest security patches to address vulnerabilities and enhance the overall security posture.
Tip 5: Monitor Device Behavior for Security Threats
Implement monitoring mechanisms like AWS IoT Device Defender or AWS IoT Analytics to track device behavior, identify anomalies, and detect potential security threats promptly.
Tip 6: Manage Device Credentials Securely
Store device credentials securely using password managers or other secure methods. Regularly rotate credentials and limit access to authorized personnel.
Tip 7: Adhere to Industry Security Standards and Regulations
Comply with relevant industry security standards and regulations, such as ISO 27001, NIST Cybersecurity Framework, and GDPR, to ensure alignment with best practices and meet legal obligations.
By following these tips, you can significantly enhance the security of your remote IoT VPC Raspberry Pi connection to AWS IoT, protecting your data, devices, and overall IoT infrastructure from potential threats.
Transition to the article's conclusion: Conclusion: Embracing a Secure Approach for Remote IoT Connectivity
Conclusion
As the adoption of IoT devices continues to expand, securing their connection to the cloud has become paramount. This article has explored the topic of securely connecting remote Raspberry Pi devices to AWS IoT via a Virtual Private Cloud (VPC), providing comprehensive insights and practical guidance.
By implementing robust authentication and authorization mechanisms, encrypting data in transit and at rest, isolating devices from the public internet, and adhering to industry security standards, organizations can establish secure and reliable connections for their remote IoT devices. Regular software updates, monitoring for security threats, and secure management of device credentials are also essential aspects of maintaining a strong security posture.
Embracing these best practices not only safeguards sensitive data and prevents unauthorized access to devices but also enables organizations to harness the full potential of IoT technology while minimizing security risks. By prioritizing security at every stage of IoT deployment, organizations can unlock new opportunities for innovation and growth while ensuring the integrity and confidentiality of their IoT infrastructure.