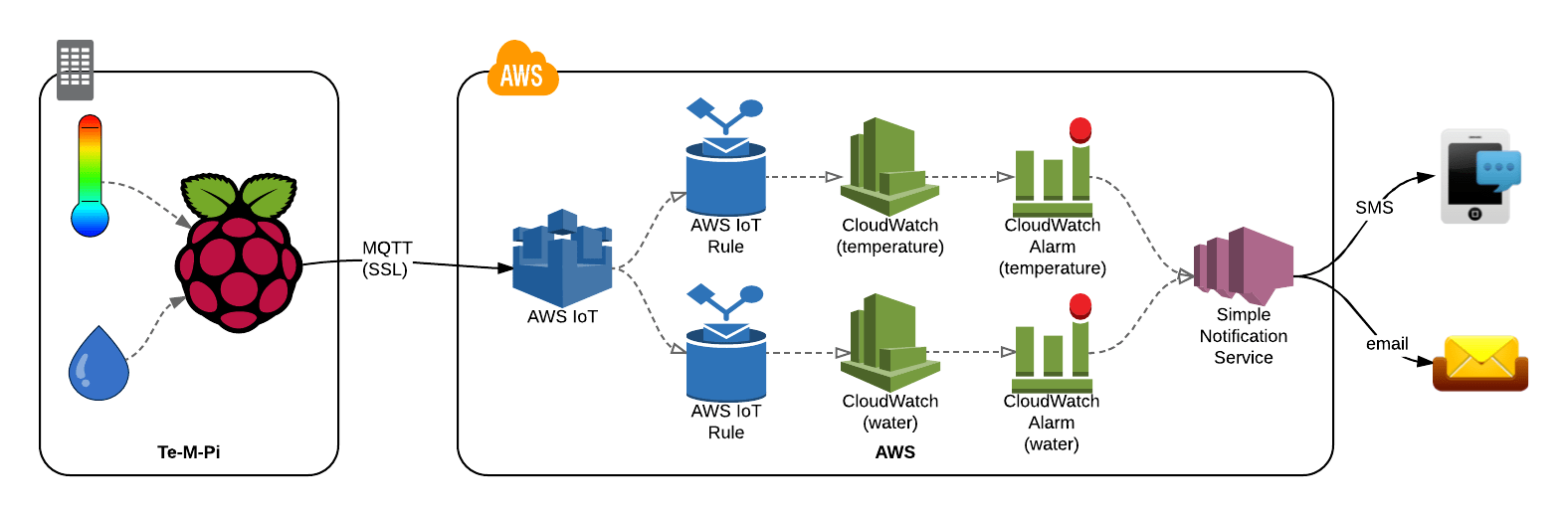
Connecting remote Internet of Things (IoT) devices to the cloud securely is crucial for businesses looking to leverage IoT's full potential. One effective way to achieve this is by utilizing a Virtual Private Cloud (VPC) on Amazon Web Services (AWS) and establishing a secure connection between the remote device and the VPC. This setup provides a private and isolated network for the IoT devices, ensuring data security and reliability.
The benefits of securely connecting remote IoT devices to an AWS VPC include enhanced security, improved performance, and simplified management. By leveraging AWS's robust security features, businesses can protect their IoT devices and data from unauthorized access and cyber threats. Additionally, the use of a VPC optimizes network performance by minimizing latency and maximizing data transfer speeds. Moreover, centralized management through the AWS console simplifies the administration and monitoring of remote IoT devices.
To establish a secure connection between a remote IoT device and an AWS VPC, several steps are typically involved, including configuring the VPC, creating a Virtual Private Gateway (VGW), and setting up a VPN connection. The process may vary depending on the specific requirements and configurations, but the overall aim is to create a secure and reliable network connection between the remote device and the AWS cloud environment.
Read also:The Life And Influence Of Caroline Fleming A Royal Journey
Securely Connect Remote IoT VPC Raspberry Pi AWS Server
Establishing a secure connection between remote IoT devices, a Virtual Private Cloud (VPC) on Amazon Web Services (AWS), a Raspberry Pi, and an AWS server involves several key aspects:
- Encryption: Data protection during transmission.
- Authentication: Verifying the identity of devices and users.
- Authorization: Controlling access to resources based on identity.
- Network Segmentation: Isolating devices and resources for security.
- Virtual Private Gateway (VGW): Connecting a VPC to an on-premises network.
- VPN Connection: Establishing a secure tunnel between devices and the VPC.
- Cloud Security Groups: Defining network access rules for devices.
- AWS IoT Core: A managed service for connecting and managing IoT devices.
These aspects work together to ensure the secure transmission of data between remote IoT devices and the AWS cloud environment. By implementing encryption, authentication, and authorization mechanisms, businesses can safeguard sensitive data and prevent unauthorized access. Network segmentation and the use of a VPN connection further enhance security by isolating devices and creating a private network for data transfer. Additionally, cloud security groups and AWS IoT Core provide additional layers of protection and management capabilities, enabling businesses to securely connect and manage their remote IoT devices.
1. Encryption: Data protection during transmission.
Encryption is a critical aspect of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It involves encrypting data during transmission to protect it from unauthorized access and interception.
- Data Confidentiality: Encryption ensures that only authorized parties can access sensitive data transmitted between devices and the cloud. It prevents eavesdropping and data breaches, maintaining the confidentiality of IoT data.
- Data Integrity: Encryption also ensures data integrity by preventing unauthorized modification or tampering during transmission. This is crucial for maintaining the reliability and trustworthiness of IoT data.
- Compliance: Encryption helps organizations meet regulatory compliance requirements related to data protection. By encrypting IoT data, businesses can adhere to industry standards and avoid potential legal liabilities.
- Enhanced Security: Encryption adds an extra layer of security to the overall system. By encrypting data, businesses can reduce the risk of data breaches and protect their IoT devices from cyber threats.
In summary, encryption plays a vital role in securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It ensures data confidentiality, integrity, compliance, and enhanced security, safeguarding sensitive data and protecting IoT systems from unauthorized access and cyber threats.
2. Authentication: Verifying the identity of devices and users.
Authentication is a crucial component of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It involves verifying the identity of devices and users attempting to access the system to prevent unauthorized access and maintain the security of the IoT environment.
The importance of authentication lies in its ability to control who and what can interact with the IoT system. By implementing robust authentication mechanisms, businesses can ensure that only authorized devices and users have access to sensitive data and resources. This helps prevent malicious actors from gaining access to the system and compromising its integrity.
Read also:Unveiling The Life And Achievements Of Aneliz Alvarezalcala
In practice, authentication can be implemented using various methods, such as:
- Device Certificates: Each device can be assigned a unique certificate that identifies it to the system. When the device attempts to connect, the certificate is presented for authentication.
- Username and Password: Users can be authenticated using a traditional username and password combination. This method is commonly used for human users accessing the system.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide additional forms of identification, such as a one-time password or a security token.
By implementing appropriate authentication mechanisms, businesses can effectively secure their IoT systems, protect against unauthorized access, and maintain the confidentiality and integrity of data.
3. Authorization: Controlling access to resources based on identity.
Authorization is a critical aspect of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It involves controlling which devices and users have access to specific resources within the system. This ensures that only authorized entities can perform actions or access data, preventing unauthorized access and maintaining the security of the IoT environment.
The importance of authorization lies in its ability to enforce fine-grained access control over the system. By implementing authorization mechanisms, businesses can define specific permissions for each device or user, limiting their ability to perform certain actions or access certain resources. This helps prevent data breaches, unauthorized changes, and malicious activities within the IoT system.
In practice, authorization can be implemented using various methods, such as:
- Role-Based Access Control (RBAC): RBAC assigns users to specific roles, each with its own set of permissions. This allows businesses to easily manage access control by granting or revoking permissions based on roles.
- Attribute-Based Access Control (ABAC): ABAC allows businesses to define access policies based on attributes, such as device type, location, or user role. This provides more granular control over access to resources.
- Identity and Access Management (IAM): AWS IAM provides a comprehensive set of tools for managing user identities and access to AWS resources. Businesses can use IAM to create users, groups, and roles, and define fine-grained access policies.
By implementing appropriate authorization mechanisms, businesses can effectively secure their IoT systems, protect against unauthorized access, and maintain the confidentiality and integrity of data.
4. Network Segmentation: Isolating devices and resources for security.
Network segmentation is a critical component of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. By isolating devices and resources onto separate networks, businesses can enhance the security of their IoT systems and mitigate the risk of unauthorized access, data breaches, and cyber threats.
The importance of network segmentation lies in its ability to limit the potential impact of a security breach. In a non-segmented network, a single compromised device can provide attackers with access to the entire network and all its resources. However, in a segmented network, the damage is contained to the specific segment where the breach occurs, preventing attackers from accessing other parts of the system.
In the context of securely connecting remote IoT devices, network segmentation can be implemented using various techniques, such as:
- VLANs (Virtual LANs): VLANs allow businesses to create multiple logical networks within a single physical network. This enables them to isolate devices and resources based on specific criteria, such as department, function, or security level.
- Firewalls: Firewalls can be used to control traffic between different network segments. By blocking unauthorized traffic, firewalls help prevent attackers from moving laterally within the network and accessing sensitive resources.
- Network Access Control Lists (ACLs): ACLs define rules that specify which devices and users are allowed to access specific network resources. By implementing ACLs, businesses can restrict access to critical resources and prevent unauthorized entities from gaining access to sensitive data.
By implementing network segmentation and using these techniques, businesses can effectively secure their IoT systems, reduce the risk of data breaches, and maintain the confidentiality and integrity of data.
5. Virtual Private Gateway (VGW): Connecting a VPC to an on-premises network.
A Virtual Private Gateway (VGW) plays a crucial role in securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It serves as a gateway between the VPC and an on-premises network, enabling secure communication between devices located in different physical locations.
The importance of a VGW lies in its ability to establish a secure and encrypted connection between the VPC and the on-premises network. This allows remote IoT devices to securely transmit data to the VPC, where it can be processed, analyzed, and stored. Without a VGW, remote IoT devices would not be able to communicate with the VPC, limiting their ability to leverage the cloud's capabilities.
In practice, a VGW can be used in various scenarios to securely connect remote IoT devices. For example, a manufacturing facility may have IoT sensors deployed on its factory floor that need to send data to a central AWS cloud platform for analysis and monitoring. By establishing a VGW between the VPC and the factory's on-premises network, the sensors can securely transmit data to the cloud, enabling real-time monitoring and predictive maintenance.
Another example is a retail store chain that wants to connect its in-store IoT devices, such as point-of-sale systems and inventory tracking sensors, to a centralized AWS cloud platform. Using a VGW, the store's on-premises network can be securely connected to the VPC, allowing the IoT devices to transmit sales data, inventory levels, and other relevant information to the cloud. This data can then be used for analytics, reporting, and business intelligence purposes.
In summary, a VGW is an essential component for securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It enables secure communication between devices located in different physical locations, allowing businesses to leverage the cloud's capabilities for IoT data collection, processing, and analysis.
6. VPN Connection: Establishing a secure tunnel between devices and the VPC.
A VPN connection is a crucial component of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It establishes a secure and encrypted tunnel between the devices and the VPC, allowing them to communicate securely over a public network, such as the internet. This is essential for protecting sensitive data and maintaining the confidentiality and integrity of IoT data.
Without a VPN connection, remote IoT devices would be vulnerable to eavesdropping, man-in-the-middle attacks, and other security threats. By establishing a VPN connection, businesses can ensure that data transmitted between the devices and the VPC is protected from unauthorized access and interception.
In practice, a VPN connection can be implemented using various technologies, such as IPsec, OpenVPN, and WireGuard. Each technology has its own advantages and disadvantages, and the choice of technology depends on factors such as security requirements, performance, and compatibility. However, all of these technologies provide strong encryption and authentication mechanisms to protect data in transit.
For example, a manufacturing facility may have IoT sensors deployed on its factory floor that need to send sensitive data, such as production data and quality control measurements, to a central AWS cloud platform for analysis and monitoring. To ensure the security of this data, the factory's network can be connected to the VPC using a VPN connection. This creates a secure tunnel between the sensors and the VPC, allowing the data to be transmitted securely over the internet.
Another example is a retail store chain that wants to connect its in-store IoT devices, such as point-of-sale systems and inventory tracking sensors, to a centralized AWS cloud platform. Using a VPN connection, the store's on-premises network can be securely connected to the VPC, allowing the IoT devices to transmit sales data, inventory levels, and other relevant information to the cloud in a secure manner.
In summary, a VPN connection is an essential component for securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It establishes a secure and encrypted tunnel between the devices and the VPC, protecting sensitive data from unauthorized access and interception, and ensuring the confidentiality and integrity of IoT data.
7. Cloud Security Groups: Defining network access rules for devices.
Cloud Security Groups are an essential component of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. They provide a way to define network access rules that control which devices can communicate with each other and with the internet. This is essential for protecting sensitive data and maintaining the security of the IoT system.
Without Cloud Security Groups, all devices on a VPC would be able to communicate with each other and with the internet without any restrictions. This would create a significant security risk, as it would allow unauthorized users to access sensitive data or launch attacks on devices on the VPC. Cloud Security Groups allow businesses to define specific rules that restrict communication between devices, reducing the risk of unauthorized access and data breaches.
For example, a manufacturing facility may have IoT sensors deployed on its factory floor that need to send data to a central AWS cloud platform for analysis and monitoring. To ensure the security of this data, the factory's network can be connected to the VPC using a VPN connection. However, the factory may also want to restrict access to the sensors from the internet. To do this, the factory can create a Cloud Security Group that allows inbound traffic from the VPC but blocks inbound traffic from the internet. This ensures that the sensors can only be accessed by authorized devices on the VPC.
Another example is a retail store chain that wants to connect its in-store IoT devices, such as point-of-sale systems and inventory tracking sensors, to a centralized AWS cloud platform. Using a VPN connection, the store's on-premises network can be securely connected to the VPC. However, the store may also want to restrict access to the IoT devices from the internet. To do this, the store can create a Cloud Security Group that allows inbound traffic from the VPC but blocks inbound traffic from the internet. This ensures that the IoT devices can only be accessed by authorized devices on the VPC.
In summary, Cloud Security Groups are an essential component for securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. They provide a way to define network access rules that control which devices can communicate with each other and with the internet. This is essential for protecting sensitive data and maintaining the security of the IoT system.
8. AWS IoT Core: A managed service for connecting and managing IoT devices.
AWS IoT Core is a managed cloud service that simplifies the process of connecting and managing IoT devices on a large scale. It provides a secure and reliable platform for collecting, processing, and storing IoT data in the cloud, making it an essential component of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server.
AWS IoT Core plays a crucial role in the secure connectivity of IoT devices by providing the following capabilities:
- Device Identity and Authentication: AWS IoT Core provides mechanisms for securely authenticating and authorizing IoT devices, ensuring that only authorized devices can connect to the platform and exchange data.
- Data Encryption: AWS IoT Core encrypts data both at rest and in transit, protecting sensitive information from unauthorized access and eavesdropping.
- Secure Communication: AWS IoT Core uses industry-standard protocols, such as MQTT and HTTPS, for secure communication between IoT devices and the cloud, ensuring data integrity and confidentiality.
- Device Management: AWS IoT Core provides a centralized platform for managing and monitoring IoT devices, allowing businesses to remotely configure devices, update firmware, and perform diagnostics.
- Device Shadows: AWS IoT Core uses device shadows to maintain the desired state of IoT devices, even when they are offline. This ensures that devices can receive updates and commands even when they are not connected, enhancing reliability and responsiveness.
By leveraging the capabilities of AWS IoT Core, businesses can securely connect and manage their remote IoT devices, enabling them to collect, process, and store IoT data in the cloud securely and efficiently. This allows businesses to gain valuable insights from their IoT data, optimize operations, and make data-driven decisions.
In summary, AWS IoT Core is an essential component of securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It provides a secure and scalable platform for connecting, managing, and communicating with IoT devices, ensuring the confidentiality, integrity, and availability of IoT data.
FAQs on Securely Connecting Remote IoT VPC Raspberry Pi AWS Server
This section addresses common questions and concerns related to securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server. It aims to provide concise and informative answers to help readers understand the key aspects of secure IoT connectivity.
Question 1: Why is it important to securely connect remote IoT devices?
Unsecured IoT devices pose significant security risks, including unauthorized access to sensitive data, device compromise, and network attacks. Secure connectivity measures protect against these threats, ensuring the confidentiality, integrity, and availability of IoT data and systems.
Question 2: What are the key components of a secure IoT connection?
Encryption, authentication, authorization, network segmentation, VPN connections, cloud security groups, and device management are all essential components of a secure IoT connection. These elements work together to protect data, control access, and maintain the integrity of IoT systems.
Question 3: How can I securely connect my Raspberry Pi to an AWS VPC?
To securely connect a Raspberry Pi to an AWS VPC, you can establish a VPN connection between the Raspberry Pi and the VPC. Additionally, you can use AWS IoT Core to manage and secure the connection, providing device authentication, encryption, and data security.
Question 4: What are the benefits of using AWS IoT Core for IoT connectivity?
AWS IoT Core offers a range of benefits, including secure device authentication, data encryption, device management, and scalability. It provides a comprehensive platform for connecting and managing IoT devices, simplifying operations and enhancing security.
Question 5: How can I improve the security of my IoT network?
Network segmentation, regular security audits, software updates, and strong access control policies are effective measures to enhance the security of your IoT network. By implementing these practices, you can reduce the risk of unauthorized access and data breaches.
Question 6: What are the common security challenges in IoT connectivity?
Common security challenges include device vulnerabilities, insecure communication channels, weak authentication mechanisms, and lack of proper data encryption. Addressing these challenges requires a comprehensive security strategy that encompasses device hardening, network security, and data protection measures.
In summary, securely connecting remote IoT devices to an AWS VPC, Raspberry Pi, and AWS server requires a multifaceted approach involving encryption, authentication, authorization, network segmentation, and device management. By implementing these measures and leveraging services like AWS IoT Core, businesses can safeguard their IoT systems, protect sensitive data, and derive maximum value from their IoT investments.
For further information and guidance on securely connecting IoT devices, refer to the AWS documentation and consult with experienced IoT security professionals.
Securely Connect Remote IoT VPC Raspberry Pi AWS Server
To establish a secure connection between remote IoT devices, a VPC on AWS, a Raspberry Pi, and an AWS server, consider the following expert tips:
Tip 1: Leverage Encryption for Data Protection
Implement robust encryption mechanisms to safeguard data during transmission. This prevents unauthorized access and ensures data confidentiality and integrity.
Tip 2: Enforce Strong Authentication and Authorization
Establish rigorous authentication protocols to verify device and user identities. Implement authorization mechanisms to control access to resources, preventing unauthorized actions and data breaches.
Tip 3: Implement Network Segmentation
Divide your network into isolated segments to limit the impact of security breaches. This strategy minimizes the potential damage caused by compromised devices and protects critical resources.
Tip 4: Utilize a Virtual Private Gateway (VGW)
Establish a secure gateway between the VPC and on-premises networks. This allows remote devices to securely communicate with the VPC, ensuring data privacy and integrity.
Tip 5: Configure Secure VPN Connections
Implement VPN connections to create encrypted tunnels between devices and the VPC. This provides an additional layer of security, protecting data from eavesdropping and unauthorized access.
Tip 6: Define Network Access Rules with Cloud Security Groups
Utilize Cloud Security Groups to define granular access rules for devices within the VPC. These rules control network traffic, preventing unauthorized communication and enhancing overall security.
Tip 7: Leverage AWS IoT Core for Device Management
Take advantage of AWS IoT Core to securely connect and manage IoT devices. This service provides device authentication, data encryption, and remote management capabilities, simplifying IoT operations and enhancing security.
Tip 8: Prioritize Regular Security Audits and Updates
Conduct regular security audits to identify and address vulnerabilities. Implement timely software updates to patch security flaws and maintain the integrity of your IoT system.
By adhering to these expert tips, you can effectively secure the connection between remote IoT devices, a VPC on AWS, a Raspberry Pi, and an AWS server. These measures ensure data protection, prevent unauthorized access, and maintain the overall security of your IoT ecosystem.
Securely Connecting Remote IoT Devices
Establishing a secure connection between remote IoT devices, a Virtual Private Cloud (VPC) on Amazon Web Services (AWS), a Raspberry Pi, and an AWS server is paramount for businesses seeking to harness the full potential of IoT. By implementing robust security measures, businesses can protect their IoT systems and data from unauthorized access, cyber threats, and data breaches.
This article has explored the key aspects of securely connecting remote IoT devices, emphasizing the importance of encryption, authentication, authorization, network segmentation, and device management. By leveraging AWS services like AWS IoT Core and utilizing best practices such as VPN connections and Cloud Security Groups, businesses can create a secure and reliable IoT ecosystem.
Securely connecting remote IoT devices is not just a technical consideration but a critical business imperative. By embracing a proactive approach to IoT security, businesses can unlock the transformative potential of IoT while safeguarding their data, devices, and reputation.